Distributed Cloud Computing
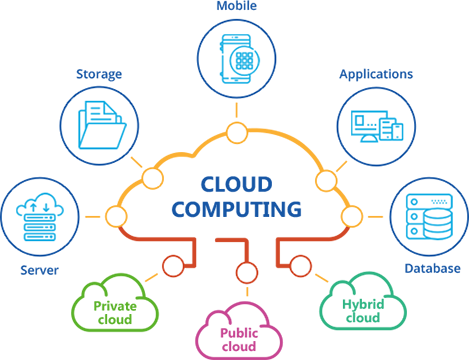
Cloud computing has revolutionized the IT world with its services provisioning infrastructure, less maintenance cost, data & services availability assurance, rapid accessibility and scalability. Cloud computing has three basic abstraction layers i.e system layer (which is a virtual machine abstraction of a server), the platform layer (a virtualized operating system of a server) and application layer (that includes web applications). Hardware layer is not included as it does not directly offer to users. Cloud computing also has three service models namely Platform as a Service (PaaS), Infrastructure as a Service (IaaS) and Software as a Service (SaaS) models. PaaS model facilitates users by providing platform on which applications can be developed and run. IaaS deliver services to users by maintaining large infrastructures like hosting servers, managing networks and other resources for clients. SaaS model makes user worry free of installing and running software services on its own machines. Presently, Salesforce.com, Google and Amazon are the leading cloud service providers who extend their services for storage, application and computation on pay as per use basis. Since Cloud computing supports distributed service oriented paradigm, multidomain and multi-users administrative infrastructure, it is more prone to security threats and vulnerabilities. Currently the biggest hurdle in cloud adoption by most of the corporate organizations is its security. Due to its distributed nature, cloud environment has high intrusion prospects and suspect of security infringements. Large business organizations place there data into Cloud and get worry-free as a Cloud service provider (CSP), stores & maintains data, application or infrastructure of cloud user. Relinquishing the control over data and application poses the challenges of security like data integrity, confidentiality and availability. Data, application and services non-availability can be imposed through Denial of Service (DOS) or Distributed Denial of Service (DDOS) attacks and both cloud service provider andusers become handicap to provide or receive cloud services. For such type of attacks Intrusion Detection System (IDS) can be emplaced as a strong defensive mechanism. IDSs are host-based, network-based and distributed IDSs. Host based IDS (HIDS) monitors specific host machines, network-based IDS (NIDS) identifies intrusions on key network points and distributed IDS (DIDS) operates both on host as well as network.
